App Security
Protect your apps, protect your business
Our platform identifies vulnerabilities early, continuously monitor threats, and keeps your apps protected around the clock.
Trusted by Customers
































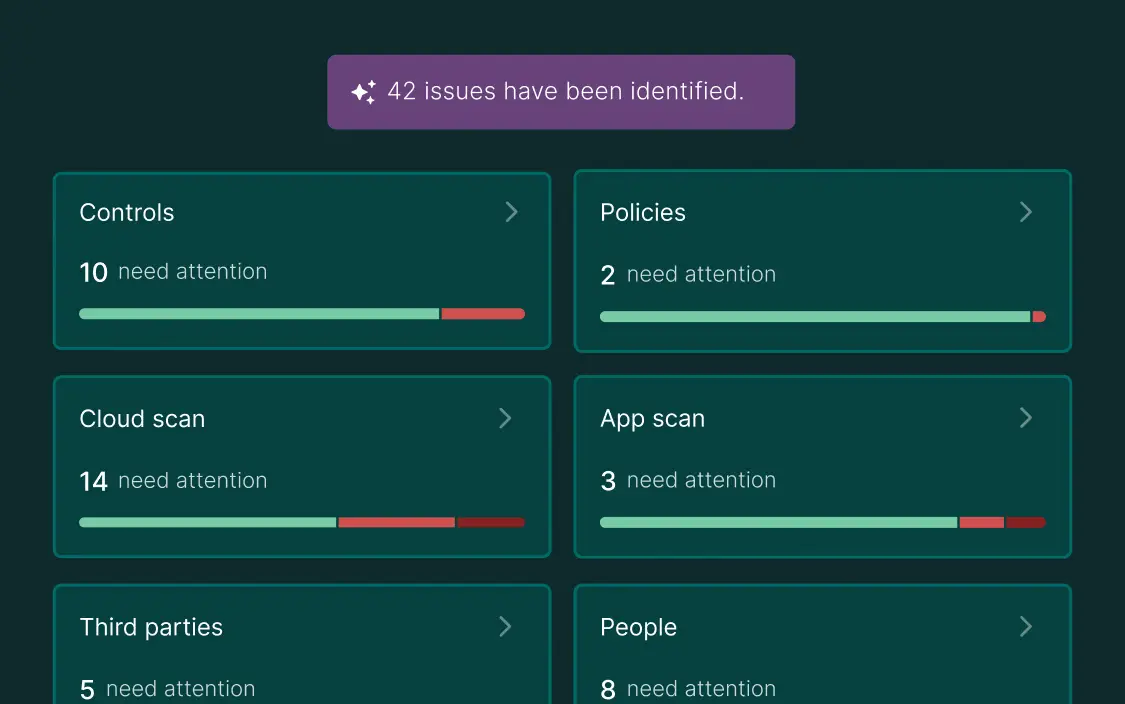
Secure your applications, stay one step ahead of hackers
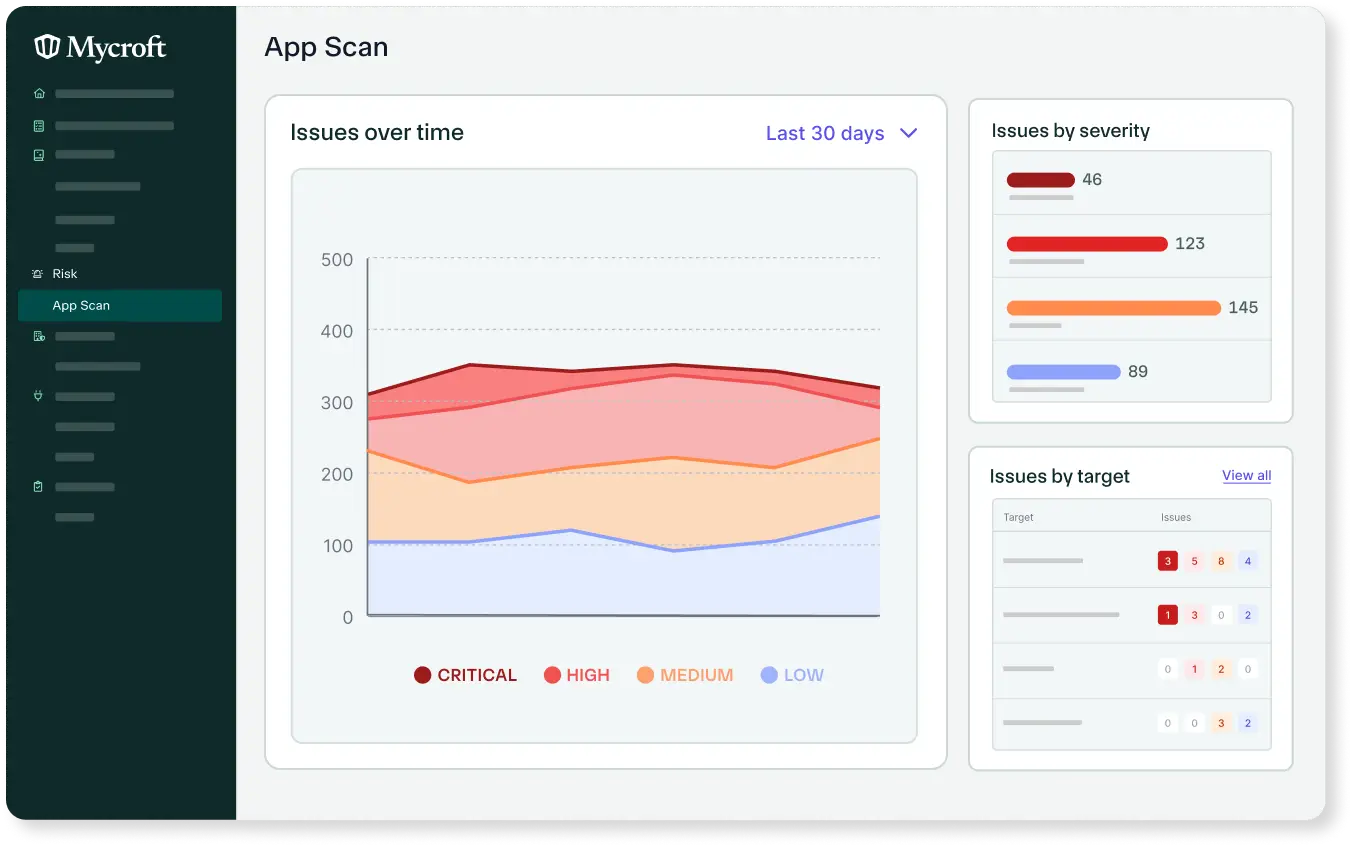
Mycroft's platform continuously monitors your applications for vulnerabilities, providing real-time insights and prioritized alerts to help you identify and fix security issues quickly.
Protect customer data
Securing your applications protects sensitive customer information, including financial details, contact information, and identity credentials, from breaches and theft.
Maintain trust
Strong application security protects sensitive data from threats and demonstrates a commitment to user safety, reinforcing long-term relationships with your brand.
Ensure business continuity
Comprehensive app security prevents disruptions caused by attacks, keeping your operations running smoothly.
Platform features
Essential features for unmatched application security
Our platform protects your applications from vulnerabilities and ensure the safety of sensitive data, allowing you to focus on innovation with peace of mind.
Monitoring
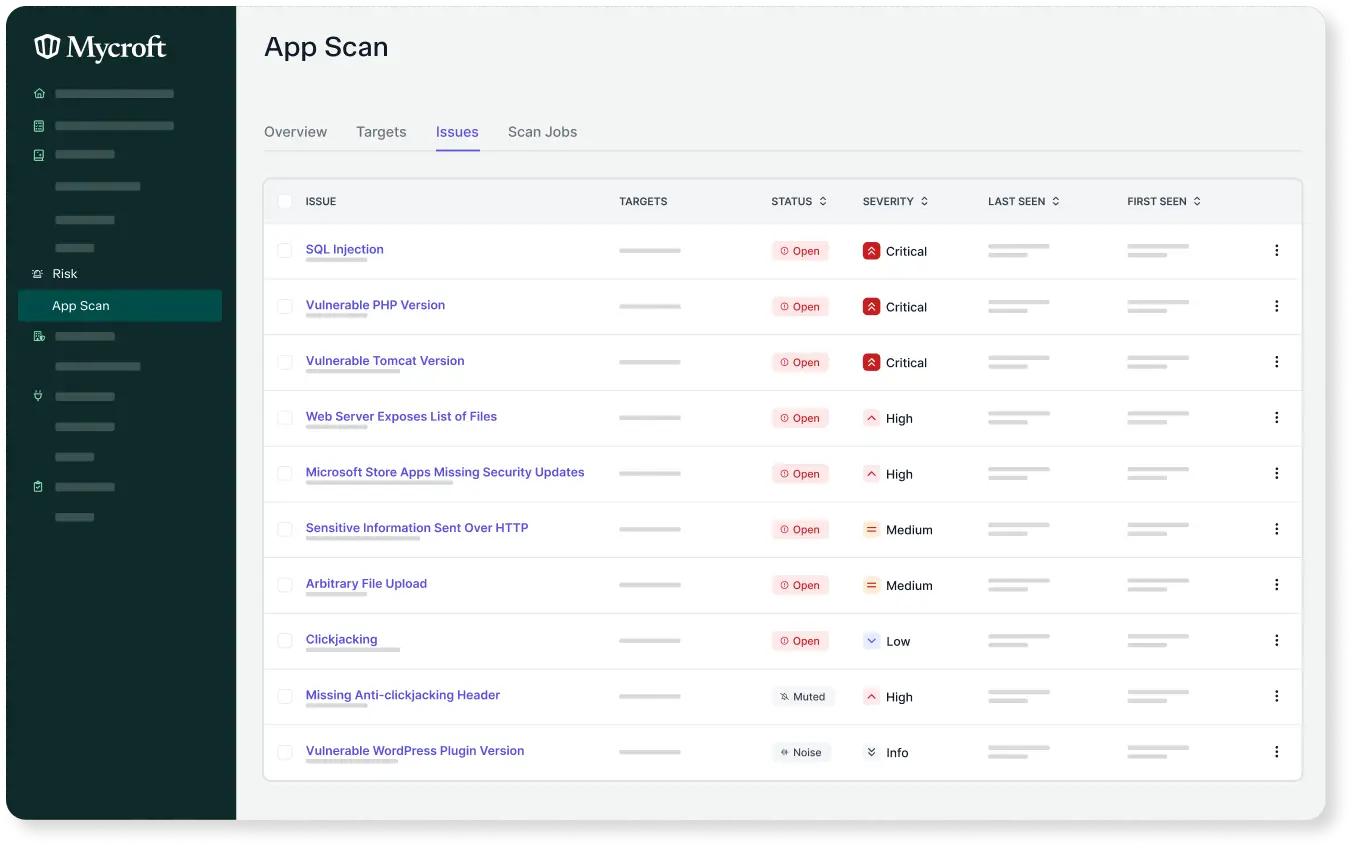
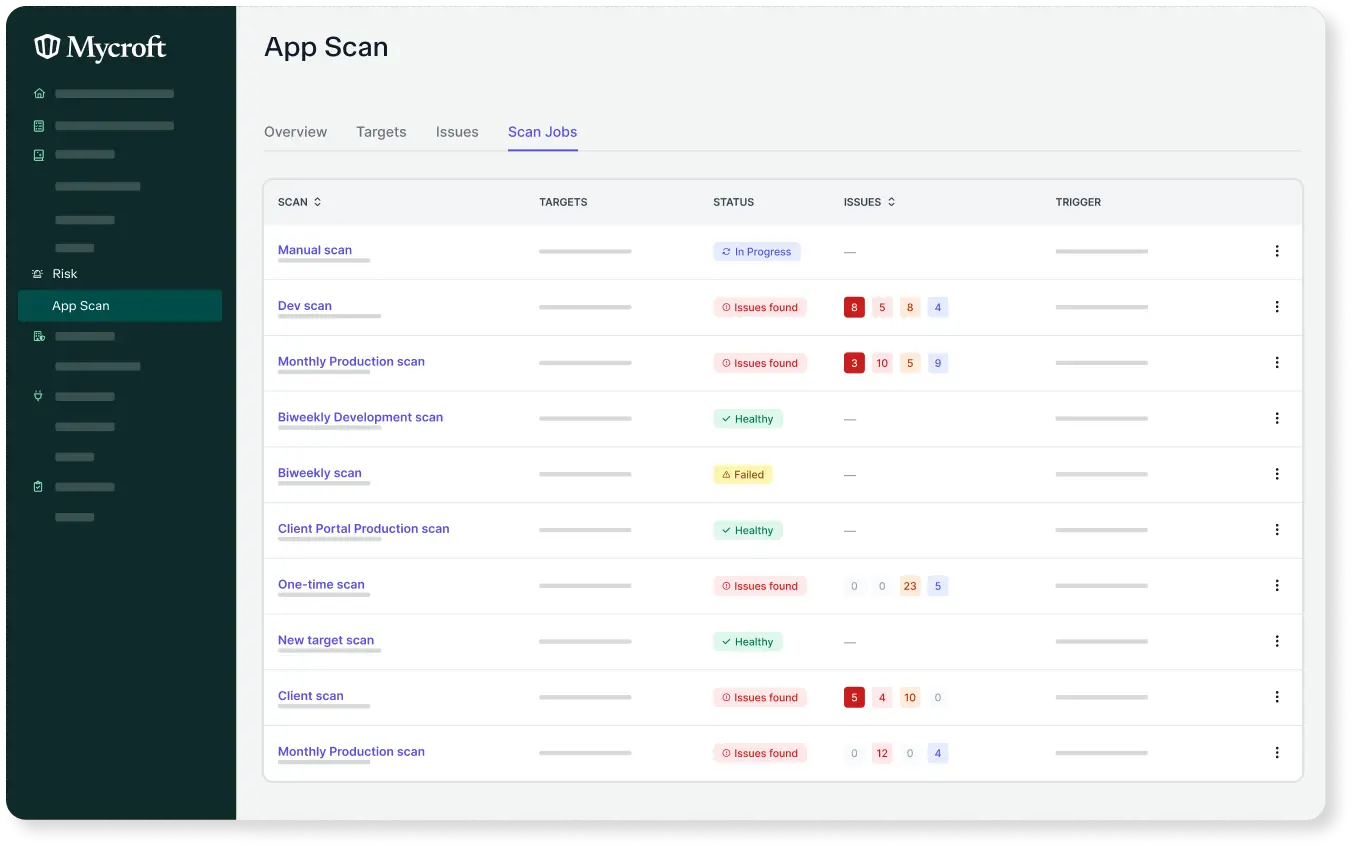
Provides real-time alerts to identify and fix issues quickly, keeping you on track.
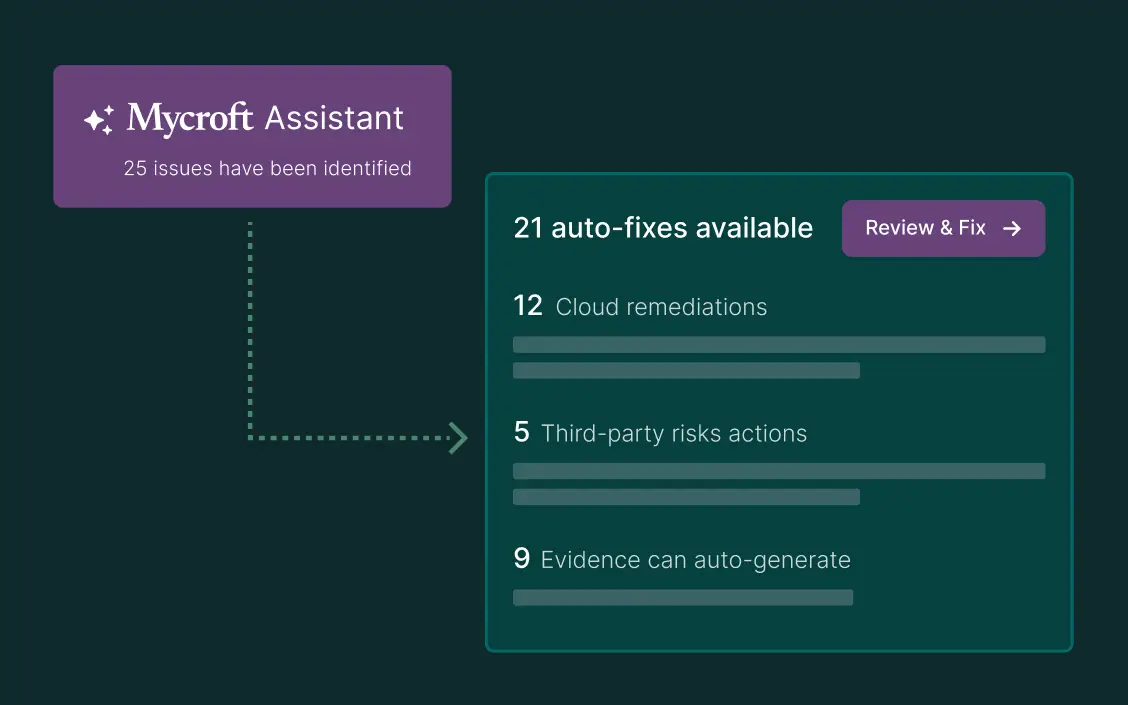
Remediation
Generates issue resolution for comprehensive application security.
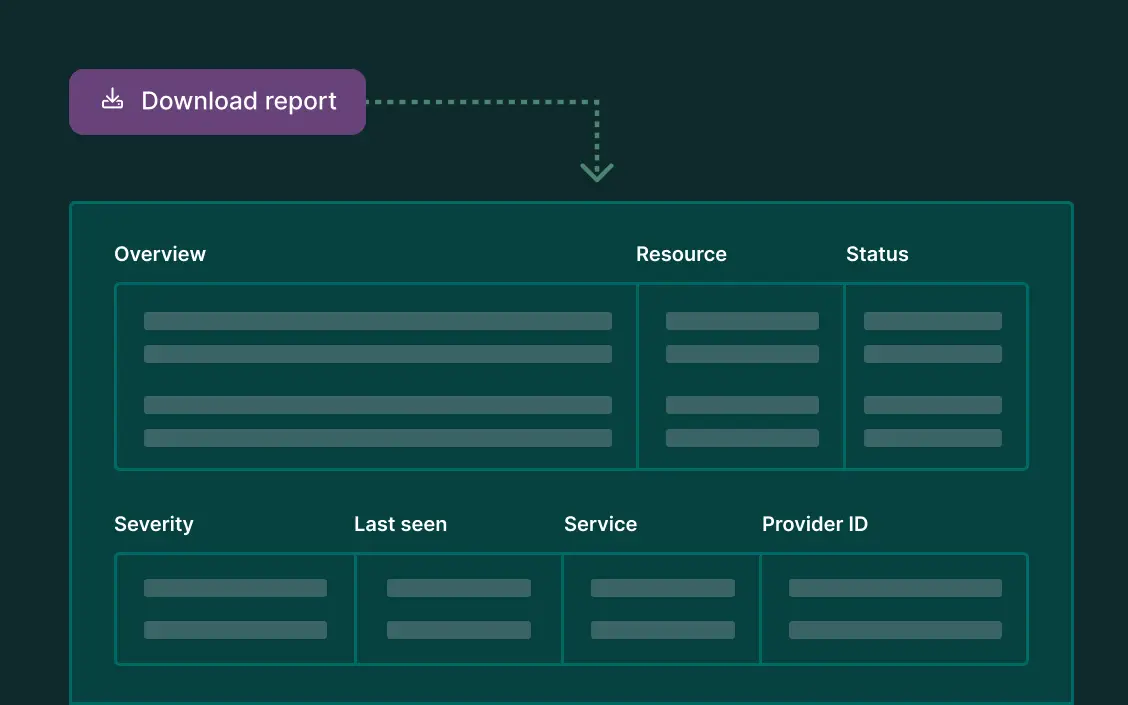
Reporting
Download scan reports for real-time updates on provider statuses and problems
Book a demo
Client Testimonial

“
Mycroft's 5-in-1 platform seamlessly consolidated our entire security stack, eliminating the need for multiple point solutions and endless checklists.”
Adam Cohen
CEO of WEAVE

Read the latest insights from our experts
Stay secure with expert, data-driven resources to strengthen your security knowledge and ensure compliance confidence.


Frequently asked questions
How can we ensure data privacy within applications?
To ensure data privacy within applications, organizations should implement strong data protection measures such as data encryption, which secures sensitive information both at rest and in transit. Additionally, incorporating strict access controls ensures that only authorized users can interact with personal data. Regularly conducting privacy assessments can help identify potential risks and vulnerabilities, while implementing data anonymization techniques can further protect sensitive information. Furthermore, it is crucial to develop and enforce data privacy policies that comply with relevant regulations, ensuring responsible handling of user data throughout the application lifecycle.
What are the main security risks associated with applications?
The main security risks associated with applications include vulnerabilities such as injection attacks, where malicious code is injected into application inputs; cross-site scripting (XSS), which allows attackers to execute scripts in a user’s browser; and insecure APIs, which can expose sensitive data if not properly secured. Additionally, applications may be at risk from improper authentication practices, leading to unauthorized access, as well as inadequate session management that can allow session hijacking. Insider threats from employees or contractors with access to application data and infrastructure also represent a significant risk. Finally, failure to keep applications updated can lead to exploitation of known vulnerabilities by attackers.
How can we implement effective incident response strategies for application breaches?
To implement effective incident response strategies for application breaches, organizations should first develop a comprehensive incident response plan that outlines clear roles, responsibilities, and procedures for handling security incidents. Regular training and simulation exercises should be conducted to ensure that all team members are familiar with the plan and can respond quickly in an actual incident. Establishing communication protocols that outline how to notify stakeholders and affected users during a breach is vital for maintaining transparency. It is also important to have monitoring and detection systems in place to quickly identify breaches, as well as conducting post-incident reviews to analyze the cause, improve response efforts, and prevent future incidents.
What is the best approach for managing data encryption in our applications?
The best approach for managing data encryption in applications involves implementing strong encryption algorithms to protect sensitive data both at rest and in transit. This can include using secure protocols such as HTTPS for data in transit and employing database encryption technologies for stored data. Organizations should also ensure that encryption keys are managed securely, using dedicated key management solutions that control access to and rotation of keys. It is essential to conduct regular audits to verify that encryption measures are being applied consistently across all applications and to stay informed about the latest encryption standards and best practices.
How can you handle security management across multiple applications?
Handling security management across multiple applications requires a unified approach that includes implementing an organization-wide security framework or policy that applies to all applications consistently. Utilizing centralized security management tools can help monitor and enforce security policies across various applications, ensuring compliance and simplifying incident response efforts. Regularly conducting security assessments and audits for each application can help identify vulnerabilities and ensure best practices are being followed. Additionally, providing training and resources to development teams across the organization will promote a security-first mindset in the application development process, allowing for proactive management of security risks across the entire application portfolio.
Stop managing tools. Start automating security.
Mycroft is the only platform that performs the full end-to-end delivery of your entire security and compliance requirements in a single platform powered by its AI Agents. Navigate security and compliance challenges without adding headcount.
Get Started




.webp)