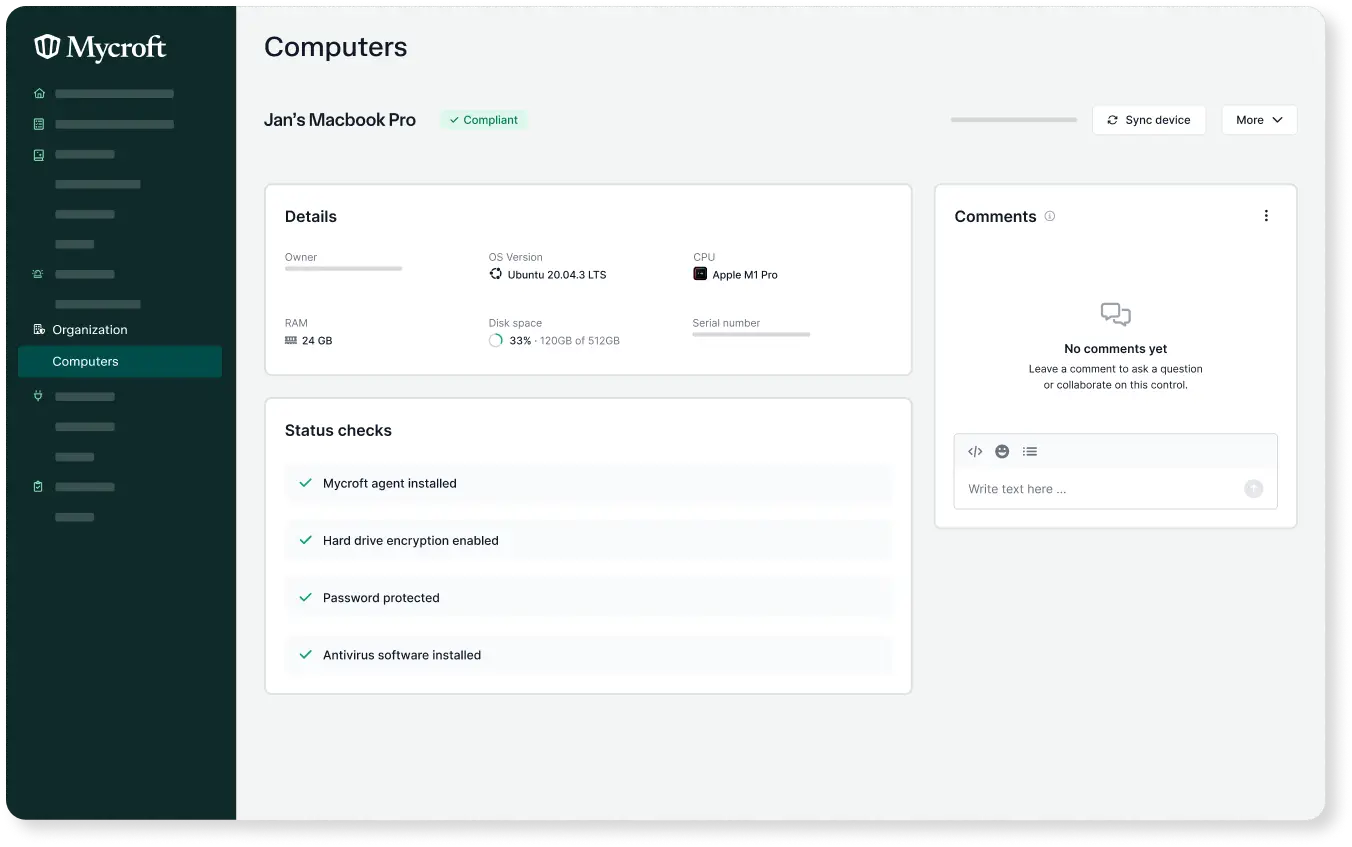
Device Management
Secure every endpoint, safeguard your business
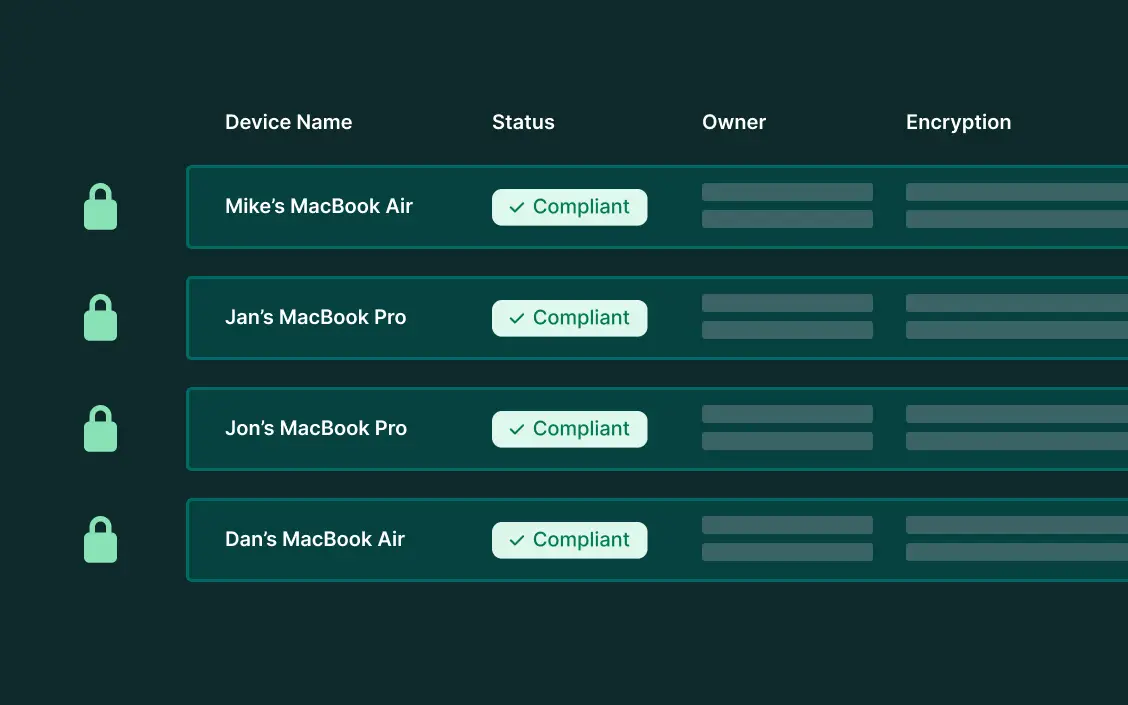
Our platform enforces security policies, monitors device health, and ensures compliance across all endpoints, keeping your business protected.
Trusted by Customers
































The foundation of strong cybersecurity
Integrating device management into your security stack helps secure endpoints, prevent vulnerabilities, and strengthen your overall cybersecurity posture.
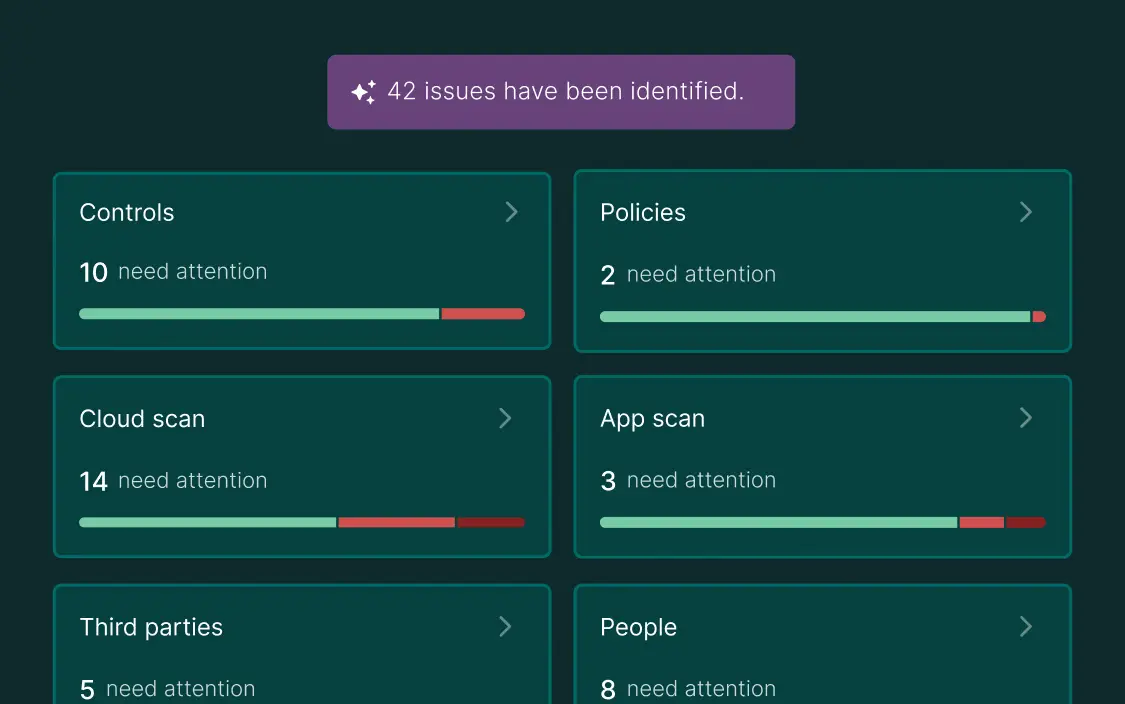
Vulnerability prevention
MDM allows for the deployment of critical updates and patches remotely, which mitigates the risk of exploitation from known vulnerabilities.
Access control
MDM ensures only authorized users and devices can access sensitive data and systems by allowing organizations to define specific permissions for users.
Data protection
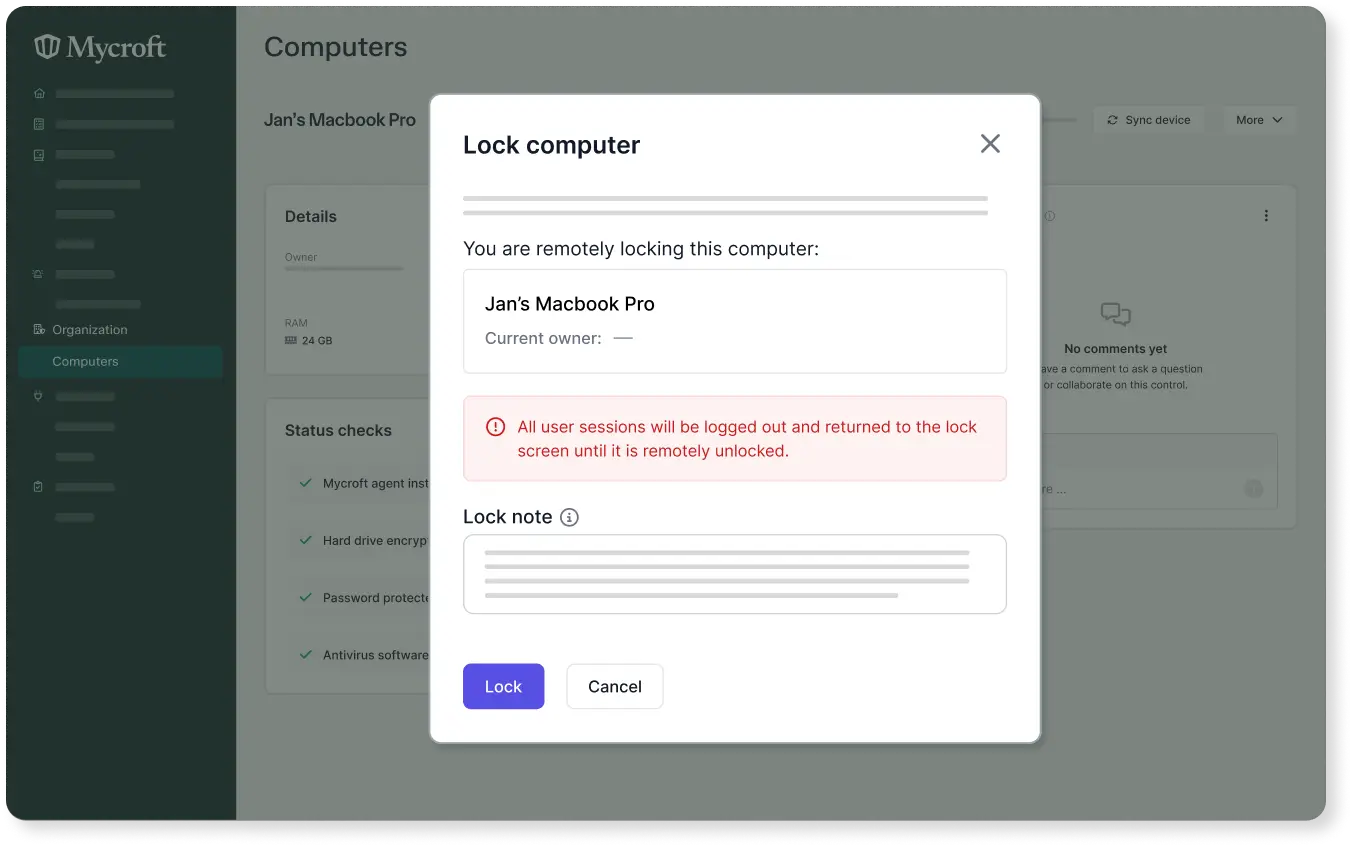
Effective device management safeguards data through encryption, remote wipe, and policy enforcement, safeguarding critical information and maintaining compliance.
Platform features
Secure your data with our comprehensive mobile device management solution
Our platform empowers organizations to safeguard sensitive information through strong encryption, remote wipe capabilities, and stringent policy enforcement
Data Encryption
Ensures all sensitive data on devices are encrypted, protecting them from unauthorized access, even in the event of theft or loss.
Monitoring
Provides real-time alerts to identify and fix issues quickly, keeping you on track.
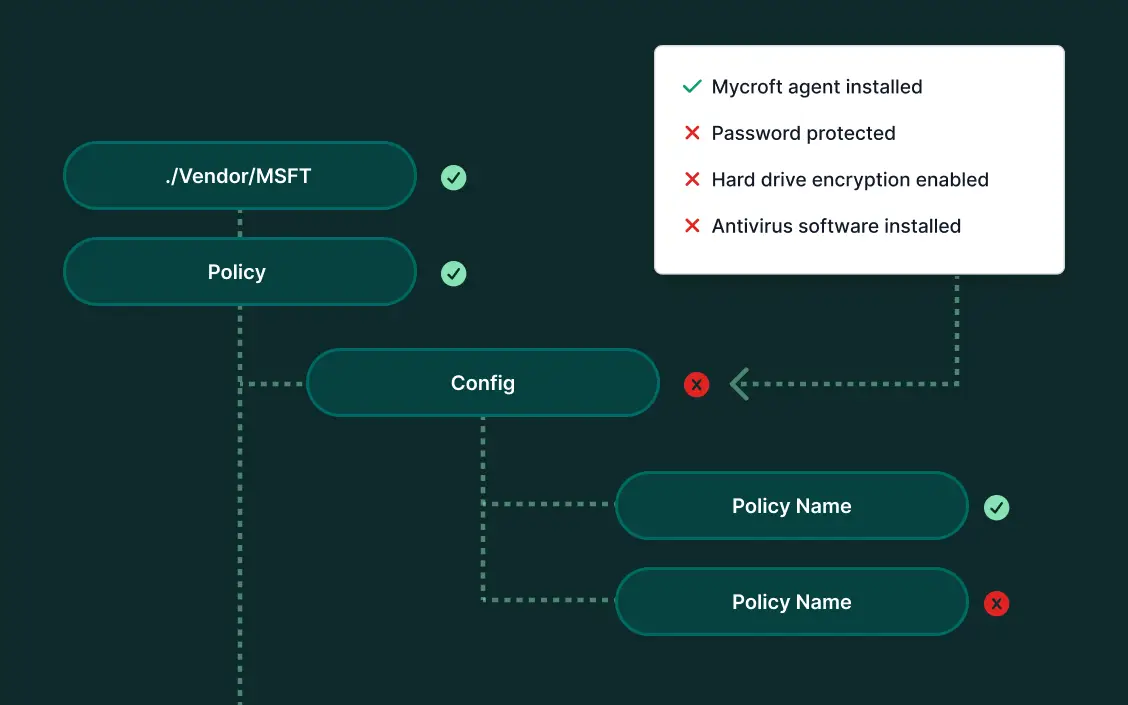
Policy enforcement
Mitigate risks associated with human error, unauthorized access, and potential data breaches.
Book a demo
Client Testimonial

“
Mycroft provided us with the best guidance through our SOC 2 process. We knew we were in good hands from the beginning.”
Steve Emmanuel
CEO & Co-founder of integratrace

Read the latest insights from our experts
Stay secure with expert, data-driven resources to strengthen your security knowledge and ensure compliance confidence.


Frequently asked questions
What are the primary cybersecurity risks associated with device management?
The primary cybersecurity risks associated with device management include unauthorized access to sensitive data due to weak authentication practices, which can lead to data breaches. Malware and malicious applications pose further threats, as they can compromise device security and potentially access corporate networks. Additionally, the risk of lost or stolen devices increases the likelihood of sensitive information being exposed if proper security measures are not in place. Insecure Wi-Fi connections can also expose devices to attacks, while vulnerabilities in device operating systems and applications can be exploited by cybercriminals to gain unauthorized access.
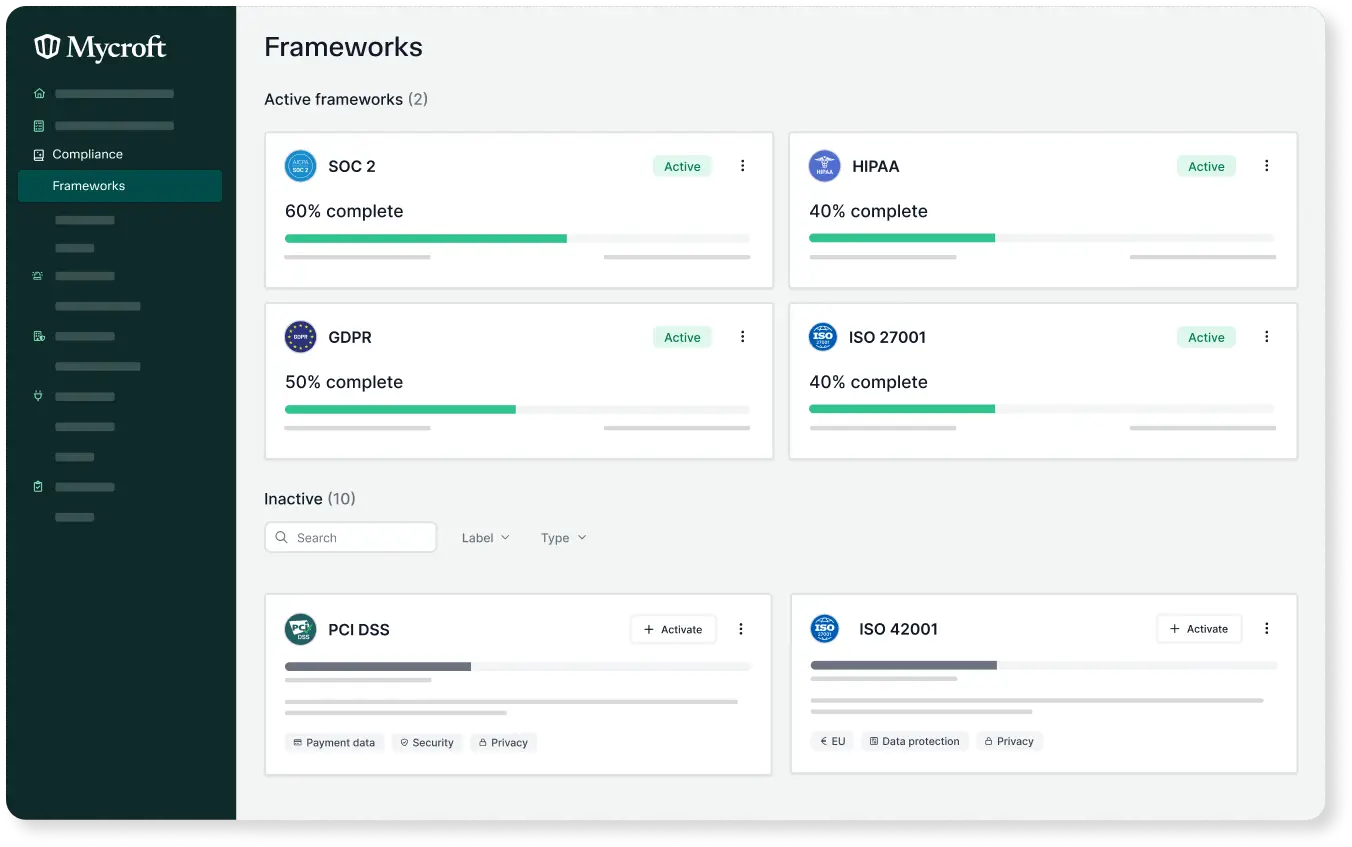
How can we enforce security policies across all managed devices?
To enforce security policies across all managed devices, organizations should implement a Mobile Device Management (MDM) solution that allows for centralized policy configuration and management. This solution can automate the enforcement of security protocols such as password complexity, encryption requirements, and remote wipe capabilities. Regular audits and compliance checks should be conducted to ensure that devices adhere to security policies, while user training and awareness programs can help reinforce the importance of compliance among employees. Additionally, incorporating automated alerts and reporting can assist in quickly identifying and addressing any deviations from established security policies.
What is the best approach for managing device access controls?
The best approach for managing device access controls involves implementing a role-based access control (RBAC) system that grants users access to only those resources and applications necessary for their job functions. Organizations should use strong authentication methods, including multi-factor authentication (MFA), to verify user identities before granting access to devices and sensitive data. Regular reviews of access permissions are essential to ensure that they remain appropriate and that any unnecessary access is promptly revoked. Additionally, using device enrollment processes during onboarding can help establish secure access controls right from the start.
How do you handle updates and patch management for devices?
Handling updates and patch management for devices requires establishing a robust routine for monitoring, testing, and deploying updates to both operating systems and applications. Organizations should utilize mobile device management (MDM) solutions to automate the distribution of software updates and patches, ensuring that devices remain up to date without significant disruption to user productivity. Scheduled maintenance windows can be established to apply updates with minimal impact on users, while detailed communication plans can inform employees about upcoming changes. It is also vital to develop a process for promptly addressing any vulnerabilities that are discovered after updates are rolled out, ensuring that devices remain secured.
How should you approach incident response for security breaches related to devices?
To effectively approach incident response for security breaches related to devices, organizations should begin by creating a detailed incident response plan that outlines specific procedures for identifying, containing, and mitigating external threats on devices. This plan should assign clear roles and responsibilities to IT staff and ensure that communication protocols are established to notify relevant stakeholders during a breach. Training employees on recognizing security incidents and reporting them promptly is crucial for maintaining a proactive security posture. Additionally, conducting post-incident reviews will help identify lessons learned and opportunities for improvement, while continuous monitoring of devices allows for the early detection of potential issues and swift response to any breaches that may occur.
Stop managing tools. Start automating security.
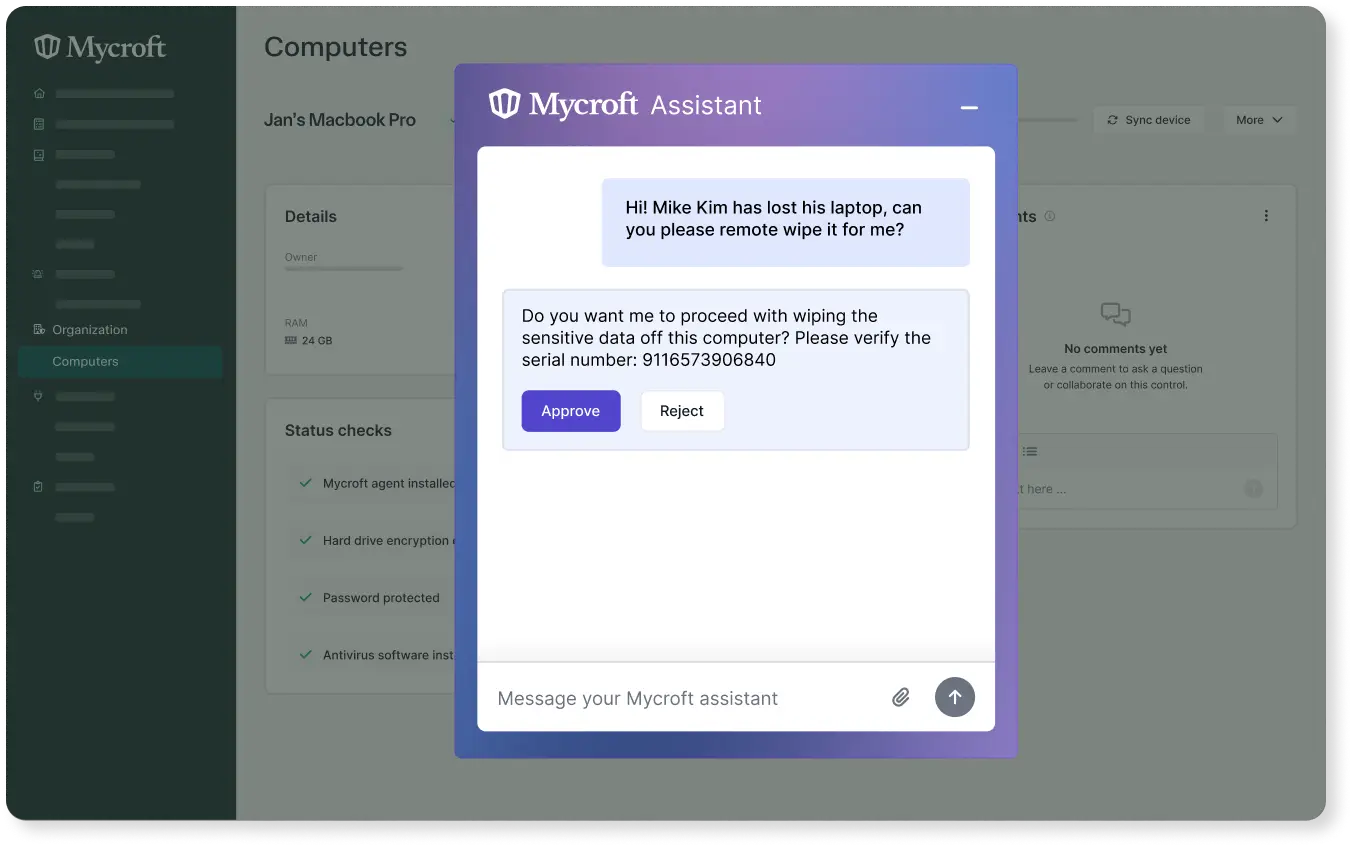
Mycroft is the only platform that performs the full end-to-end delivery of your entire security and compliance requirements in a single platform powered by its AI Agents. Navigate security and compliance challenges without adding headcount.
Get Started



.webp)