Third-Party Risk Management
Keep external threats at bay with strong TPRM
Our platform provides visibility and control over external vulnerabilities, helping your organization stay secure, compliant, and protected from outside threats.
Trusted by Customers
































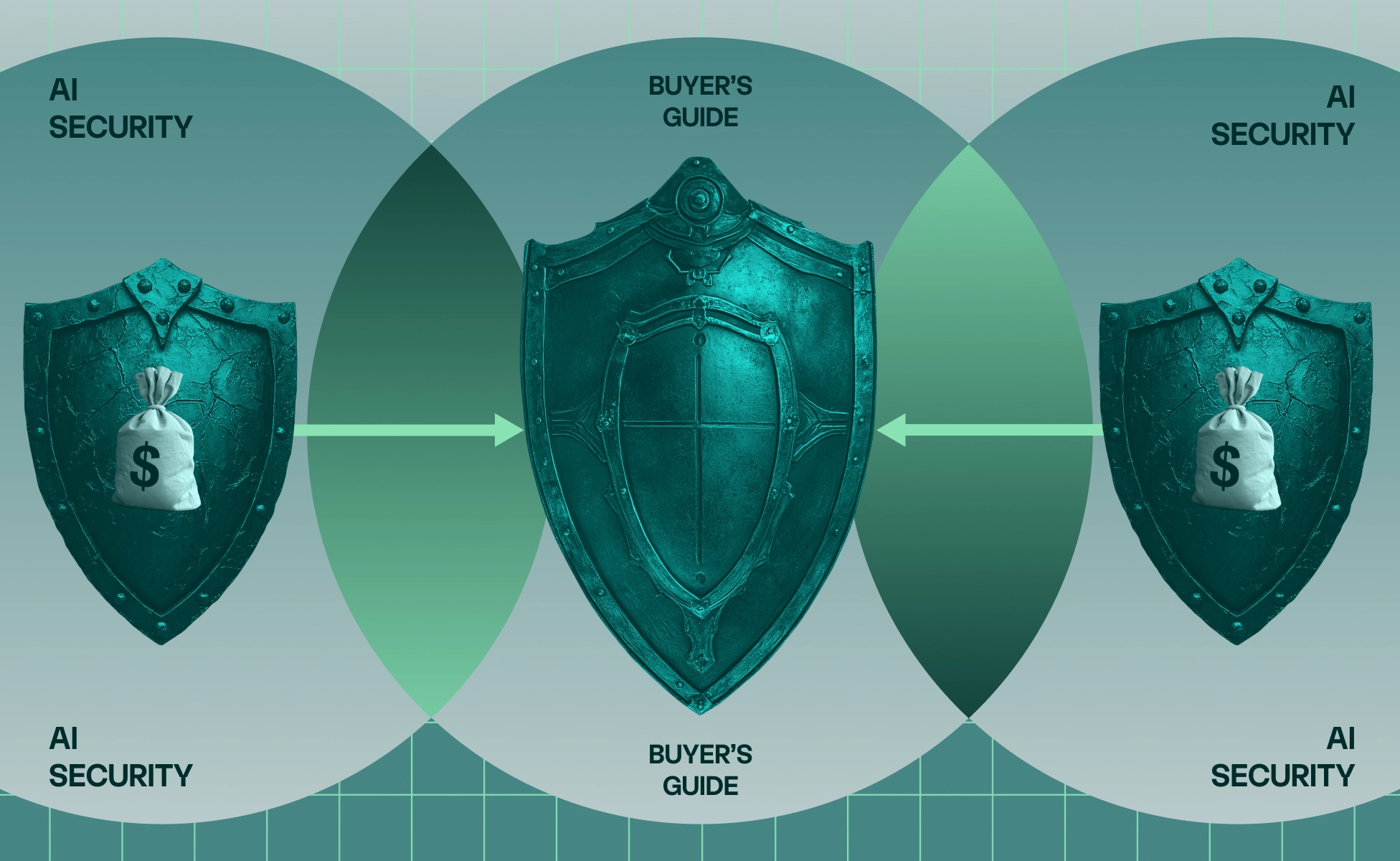
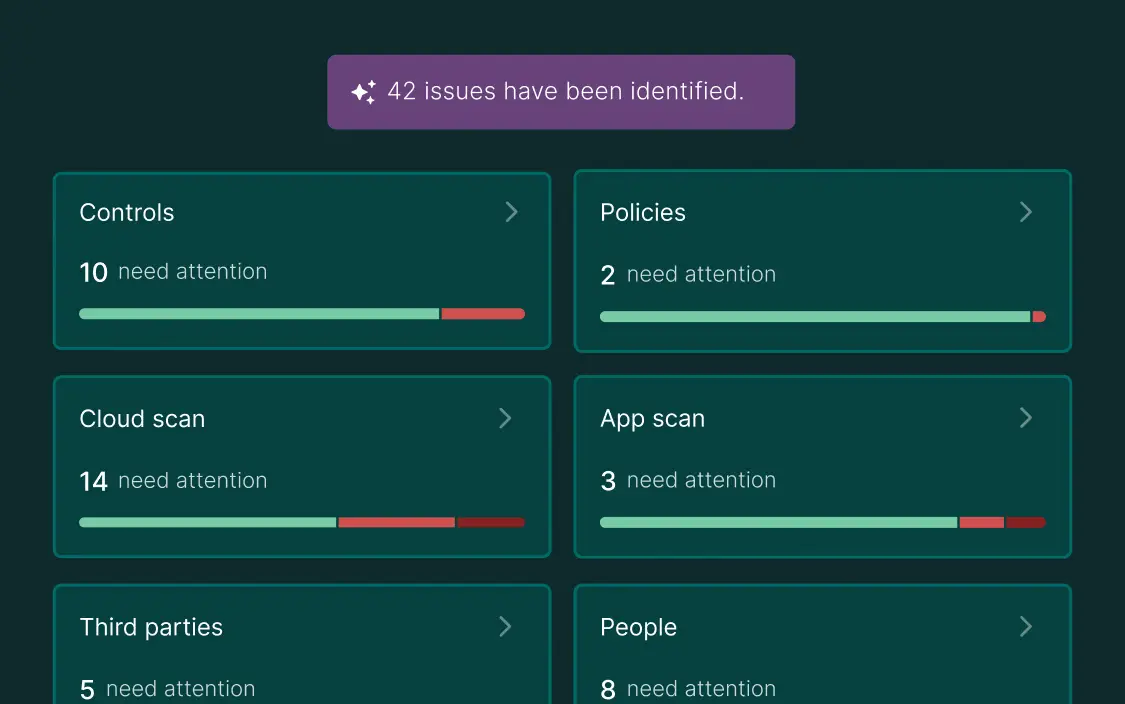
How strong third-party risk management shields your business
Strong third-party risk management identifies vulnerabilities, enforces security standards, and monitors risks continuously to protect your organization from external threats.
Early identification of vulnerabilities
It helps you assess and identify potential security gaps in third-party vendors before they can be exploited, reducing the risk of breaches.
Enforcement of security standards
It ensures that all external partners adhere to your company's security protocols and compliance requirements, preventing weak links in your security chain.
Continuous monitoring
Ongoing oversight of third parties allows proactive detection of emerging threats or changes in risk levels, enabling timely responses to minimize potential security incidents.
Platform features
Manage TPRM risks effectively with our platform
Prioritize your high-risk relationships with our platform by providing clear insights into vendor assessment statuses, criticality levels, and compliance metrics.
Monitoring
Real-time signals from your vendor ecosystem—security, compliance, access, and changes that matter—without manual check-ins.
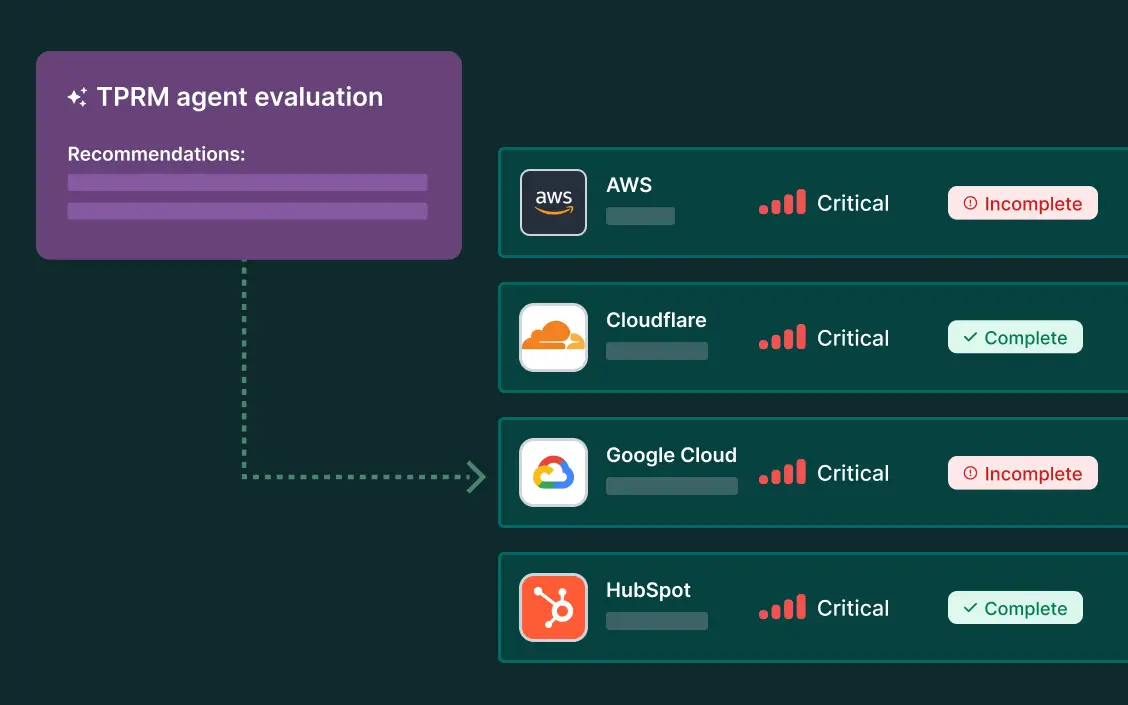
Risk triage & prioritization
A clear view of your highest-risk vendors, why they’re risky, and what to do next—ranked by impact and criticality.
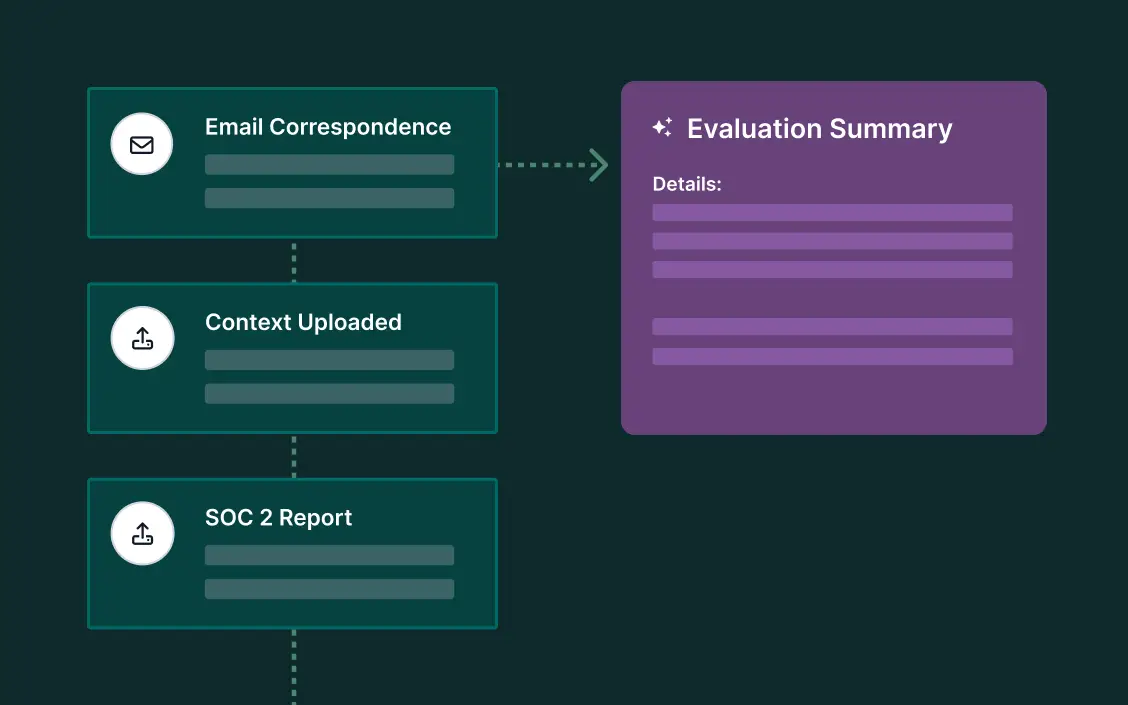
Automated workflows
Kick off reviews, collect evidence, request attestations, and track remediation with automated tasks, reminders, and approvals.
Book a demo
Client Testimonial

“
Mycroft has made compliance so incredibly painless – this is exactly the type of service people need.”
Michael Swan
COO of Paidiem

Read the latest insights from our experts
Stay secure with expert, data-driven resources to strengthen your security knowledge and ensure compliance confidence.


Frequently asked questions
What specific cybersecurity threats do we face when working with third-party vendors?
When working with third-party vendors, organizations face specific cybersecurity threats such as unauthorized access to sensitive data due to inadequate security practices by the vendor, which can lead to data breaches. Additionally, third-party vendors may introduce vulnerabilities through insecure systems or software, making them a potential target for cyber attacks. The risk of supply chain attacks also increases, where malicious actors exploit weaknesses in a vendor’s infrastructure to gain access to clients’ systems. Furthermore, compliance risks arise if vendors fail to adhere to applicable regulations or security standards, potentially placing the organization at risk of penalties and reputational damage.
What ongoing monitoring practices are necessary for third-party vendors?
Ongoing monitoring practices for third-party vendors should include regular assessments of their security posture through audits, reviews, and performance evaluations to ensure they continue to meet established security standards. Utilizing continuous monitoring solutions such as security ratings services can provide real-time insights into vendors’ security practices and any emerging vulnerabilities. Organizations should also monitor the vendor's compliance with relevant regulations and contractual obligations, along with establishing communication channels to promptly address any security incidents or changes in the vendor's risk profile. Lastly, conducting periodic reviews of the data shared with vendors helps to ensure ongoing appropriateness and security of sensitive information.
How can we manage data sharing and access with third-party vendors securely?
To manage data sharing and access with third-party vendors securely, organizations should adopt strict data governance policies that specify what data can be shared and under what conditions. Implementing role-based access controls limits vendor access to only the information necessary for their operations, while encryption should be used to protect sensitive data both in transit and at rest. Establishing secure communication protocols, such as VPNs or secure file transfer methods, helps to safeguard the data exchange process. Additionally, regularly reviewing data-sharing agreements and ensuring that they include adequate data protection measures is crucial for maintaining a secure partnership with vendors.
What are best practices for risk assessments and audits of third-party vendors?
Best practices for risk assessments and audits of third-party vendors include conducting comprehensive due diligence during the vendor selection process, which involves assessing their security policies, compliance history, and incident response capabilities. Organizations should standardize their risk assessment methodology to ensure that all vendors are evaluated consistently and adequately. A risk-based approach should be applied by classifying vendors into criticality tiers (for example: Critical, High, Medium, and Low) based on factors such as data sensitivity, system access, and business impact. This tiering should drive the depth of assessment and review cadence such as annual reviews for Critical vendors, semi-annual or annual reviews for High-risk vendors, and periodic or event-driven reviews for Medium and Low-risk vendors. Rather than relying on blanket audit schedules, organizations should leverage targeted reassessments, external assurance artifacts (e.g., SOC reports), and ongoing monitoring signals to validate continued alignment with security and compliance expectations. All assessment results, identified gaps, and remediation actions should be documented and tracked over time to demonstrate oversight, support risk decisions, and identify systemic trends.
What actions should we take if a vendor is found to have significant security vulnerabilities?
If a vendor is found to have significant security vulnerabilities, organizations should first engage in open communication with the vendor to understand the nature and potential impact of the issues. Collaboratively develop a remediation plan with specific timelines and resources to address the vulnerabilities effectively. During this period, organizations may need to enforce temporary access restrictions or implement additional security measures to safeguard sensitive data until the vendor resolves the issues. Continuous monitoring should be implemented to assess the vendor's progress toward remediation, and a follow-up assessment should be conducted to evaluate the effectiveness of the implemented fixes. If necessary, organizations should be prepared to evaluate alternative vendors or contingency plans in case the vulnerabilities pose an ongoing risk.
What are fourth parties, and how do they impact our TPRM efforts related to cybersecurity, particularly concerning Critical User Entity Controls (CUECs)?
Fourth parties, often referred to as "sub-vendors" or vendors of vendors, are organizations that provide services or products to third parties that, in turn, serve your organization. They can significantly impact your TPRM efforts since vulnerabilities or security weaknesses at this level can introduce risks that cascade through the supply chain and potentially affect your organization’s security posture. To manage these risks effectively, it is important to identify which fourth parties are connected to your third-party vendors and to assess the security controls and practices they have in place. Critical User Entity Controls (CUECs) refer to the key security measures that organizations implement to mitigate risks associated with third parties, including fourth parties. These controls serve to protect critical assets and data, ensuring that third and fourth parties comply with established security standards. It is essential to include CUECs in your risk assessments and monitoring practices to create a comprehensive view of the security landscape involving all levels of suppliers in your supply chain. This holistic approach helps to ensure that you are not only protecting your data from third-party risks but also extending that protection to the entire vendor ecosystem.
Stop managing tools. Start automating security.
Mycroft is the only platform that performs the full end-to-end delivery of your entire security and compliance requirements in a single platform powered by its AI Agents. Navigate security and compliance challenges without adding headcount.
Get Started





.webp)